Background: While conducting a penetration test of a client’s external network, I discovered a way to enumerate users’ in ManageEngine’s ADSelfService Plus application. This allows an attacker to determine the […]


Background: While conducting a penetration test of a client’s external network, I discovered a way to enumerate users’ in ManageEngine’s ADSelfService Plus application. This allows an attacker to determine the […]

Background While conducting a penetration test for a customer, I encountered an unused developer forum using JForum version 2.1.8 and started looking for vulnerabilities within the application. Version Tested: 2.1.8 CVE […]
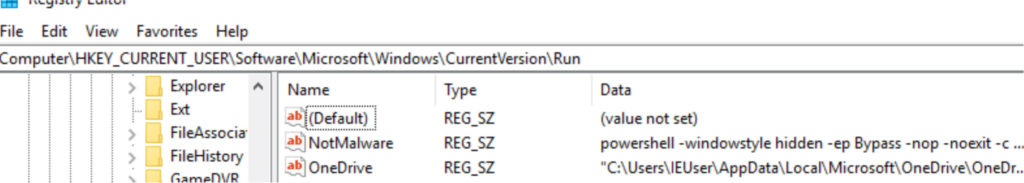
Background In previous roles focused on malware analysis and defense, a recurring trend observed across the industry has been the rise of fileless malware, particularly the use of mshta.exe as […]

From Jonathan Swift’s fake almanac in 1708 to the modern Dihydrogen monoxide joke, hoaxes have been around for as long as humans have enjoyed deceiving each other for fun. The ease of communication […]

Just over a month ago, Marriott International, one of the world’s largest hotel chains, announced that there was unauthorized access to the database, which contained guest information relating to reservations at […]

Background: Recently I’ve seen a decent number of privilege escalations occurring on Windows due to permission issues and using symlinks. The work from Ryan Hanson from Atredis on the Cylance privilege escalation and Windows Standard […]

CVE Numbers: CVE-2018-0437 – Cisco Umbrella ERC releases prior to 2.1.118 and Cisco Umbrella CVE-2018-0438 – Cisco Umbrella ERC releases prior to 2.1.127 Versions Tested: Umbrella Roaming Client 2.0.168 Security Advisories: https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20180905-umbrella-priv https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20180905-umbrella-file-read Binary Planting: […]

Security awareness training is broken. Read the news any day of the week and you can find articles talking about breaches, ransomware attacks, and countless records stolen resulting in identity […]

Exploits for network devices including routers, switches, and firewalls have been around for as long as networking has been a thing. It seems like every week a researcher discloses a […]

Introduction Finding Linux servers heavily reliant on Sudo rules for daily management tasks is a common occurrence. While not necessarily bad, Sudo rules can quickly become security’s worst nightmare. Before […]