Background In previous roles focused on malware analysis and defense, a recurring trend observed across the industry has been the rise of fileless malware, particularly the use of mshta.exe as […]
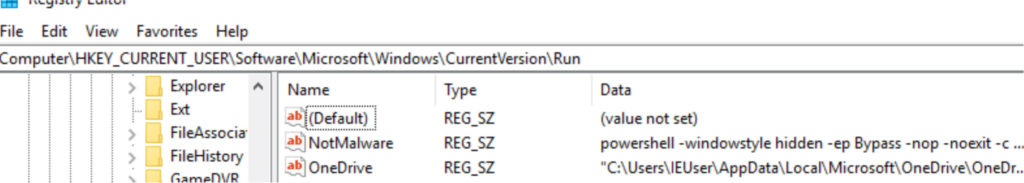

Background In previous roles focused on malware analysis and defense, a recurring trend observed across the industry has been the rise of fileless malware, particularly the use of mshta.exe as […]

Background: Recently I’ve seen a decent number of privilege escalations occurring on Windows due to permission issues and using symlinks. The work from Ryan Hanson from Atredis on the Cylance privilege escalation and Windows Standard […]

CVE Numbers: CVE-2018-0437 – Cisco Umbrella ERC releases prior to 2.1.118 and Cisco Umbrella CVE-2018-0438 – Cisco Umbrella ERC releases prior to 2.1.127 Versions Tested: Umbrella Roaming Client 2.0.168 Security Advisories: https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20180905-umbrella-priv https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20180905-umbrella-file-read Binary Planting: […]

Exploits for network devices including routers, switches, and firewalls have been around for as long as networking has been a thing. It seems like every week a researcher discloses a […]

Introduction Finding Linux servers heavily reliant on Sudo rules for daily management tasks is a common occurrence. While not necessarily bad, Sudo rules can quickly become security’s worst nightmare. Before […]