By Trevor Olson
Recently, SlashNext (and many others) published an interesting article on ‘SessionShark,’ a phishing-as-a-service toolkit designed to steal session tokens and bypass Microsoft MFA. Their discussion around the topic was interesting and highlights the evolving tactics of cybercriminals. (Source: “SessionShark Steals Session Tokens to Slip Past Office 365 MFA)
From my perspective, there is a lot of discussion around the topic of SessionShark’s phishing-as-a-service and an implication that it is wildly new, unique and a huge issue that we as security professionals are going to have to face. Some have even gone so far as to call it the “death of Microsoft MFA.”
But as security leaders, our role shouldn’t be to jump to hyper reactionary and alarmist responses — it’s to maintain perspective, strengthen fundamentals, and guide our organizations with calm, strategic action.
Rather than panic, organizations should take this moment to reinforce a security-first approach that’s already proven effective against evolving attacks.
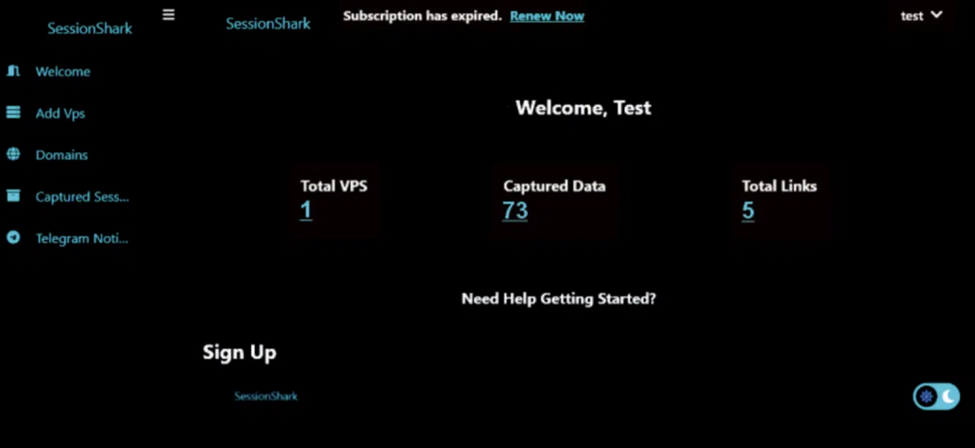
Source: Image courtesy of SlashNext’s article linked above
1. Start with User Education
The most critical defense against SessionShark and phishing attacks in general remains user awareness.
Organizations must prioritize consistent, practical security training for employees. Key behaviors to reinforce include:
- Always verifying URLs before logging in
- Using trusted bookmarks for critical systems
- Being skeptical of unexpected authentication prompts or login requests
Phishing remains the most common and effective attack vector not because our tools have failed, but because users are human. Empowering people remains our first and best line of defense.
2. Implement Privileged Identity Management (PIM)
Beyond frontline defenses, organizations must limit the potential impact of any compromised accounts.
Implementing Microsoft Entra Privileged Identity Management (PIM) ensures administrative rights are granted only when needed and only for as long as needed.
By reducing standing privileges, we reduce the potential blast radius of a stolen session token — containing risks before they become breaches.
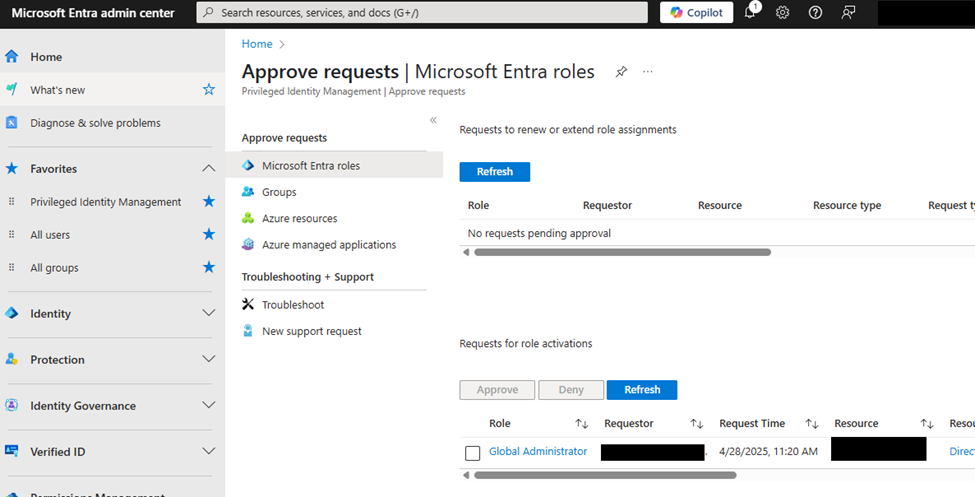
Source: Microsoft Entra’s PIM permission checkout approval screen
3. Strengthening Technical Defenses
Microsoft offers layered protections through both Exchange Online Protection (EOP) and Defender for Office 365. Organizations that have these properly configured are already well-positioned against attacks like SessionShark.
Exchange Online Protection (EOP) – Baseline Protections:
- Spoof intelligence – Detects and blocks attempts to impersonate trusted domains.
- Anti-phishing policies – Protect against known phishing behaviors and patterns.
- DMARC enforcement – Verifies domain authenticity and prevents unauthorized spoofing.
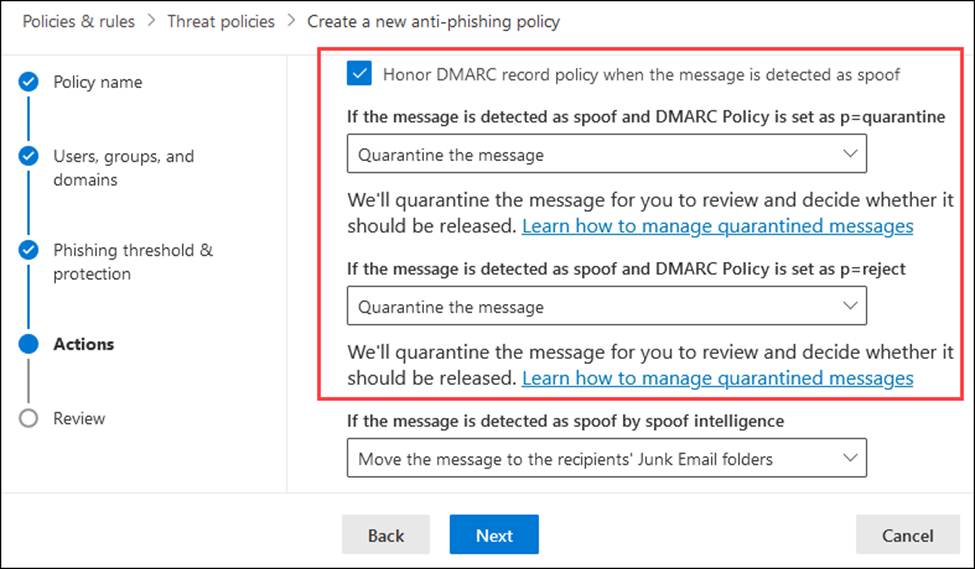
Source: https://learn.microsoft.com/en-us/defender-office-365/anti-phishing-policies-about
Microsoft Defender for Office 365 – Advanced Protections:
- Safe Links – Scans and rewrites URLs to prevent post-delivery attacks.
- Safe Attachments – Analyzes file behavior to block malicious payloads.
- Real-time phishing detection – Identifies emerging threats using AI-based models.
- Attack simulation training – Delivers customizable phishing simulations to proactively train employees.
- Continuous Access Evaluation (CAE) – Enables real-time session enforcement and token invalidation.
4. Understand Your Microsoft Licensing
Many organizations already own the capabilities they need to defend against these attacks but may not have fully deployed them simply because they are not aware that the features are included with their already existing licensing.
- Microsoft 365 E3 includes:
- Microsoft Entra ID P1 (Conditional Access, identity protection)
- Microsoft Defender for Endpoint Plan 1 (next-gen AV protection, attack surface reduction)
- Microsoft 365 E5 includes:
- Microsoft Entra ID P2 (adds Privileged Identity Management and risk-based Conditional Access)
- Microsoft Defender for Office 365 Plan 2 (advanced email threat protection and automation)
- Microsoft Defender for Endpoint Plan 2 (advanced threat hunting and automated investigation)
If you’re already on E5 (or even E3 plus Defender Plan 2 add-ons), you’re paying for these protections.
The next step is ensuring they are properly configured and aligned to your threat model.
5. Keep Perspective: This Is Evolution, Not Revolution
While SessionShark’s token theft approach is sophisticated, it’s not unprecedented.
Session hijacking and adversary-in-the-middle (AiTM) tactics have existed for years.
What’s changing is the accessibility of these tools not the fundamental nature of the threat.
Strong security hygiene still wins:
- Educated users
- Limited privileges
- Layered phishing defenses
- Real-time detection and response
The emergence of tools like SessionShark reminds us that cybersecurity resilience is not built on single technologies, but on layered defenses, proactive strategies, and an empowered user base.
So, to close things out, Microsoft MFA is not dead. Security strategy simply needs to evolve alongside attacker tactics.