Threat actors thrive on stolen credentials, and enterprise emails are often their top prize. While much attention is given to zero-days and vulnerabilities, leaked credentials from third-party data breaches are one of the most common—and overlooked—entry points.
What’s the Risk?
Leaked corporate credentials are frequently used in password spraying, credential stuffing, and phishing attacks. If an attacker obtains a valid corporate email and password combo from a prior breach (e.g., LinkedIn, Dropbox, or Adobe), they can attempt to access enterprise resources.
Understanding Credential Reuse in the Enterprise
Employees often reuse passwords across personal and professional accounts. When a consumer service suffers a breach and the login includes a work email, that same password could be the key to your internal tools, VPN, email accounts, or cloud portals.
Using HaveIBeenPwned (HIBP) to Find Breached Emails
To detect whether your organization’s emails have appeared in known breaches, you can leverage the HaveIBeenPwned (HIBP) API. HIBP is a public service that tracks credentials found in breaches and makes them searchable.
Here’s a basic Python script that uses HIBP to identify where a list of emails have been compromised:
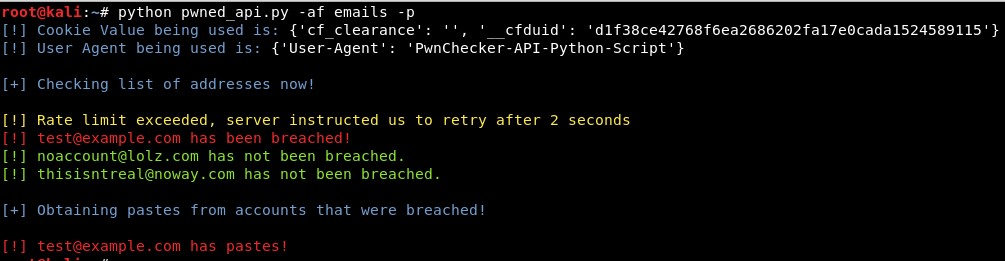
Note: You will need a valid HIBP API key. Consider rate limits and API usage guidelines.
Next Steps After Discovery
If you find compromised emails:
- Reset Passwords Immediately – Especially for any shared credentials or single sign-on (SSO) accounts.
- Implement MFA Everywhere – Even breached credentials are worthless with strong multi-factor authentication.
- Educate Employees – Ensure your team understands the importance of not reusing passwords and how attackers use breach data.
- Continuous Exposure Monitoring – Monitor new data breaches as they appear. Services like HIBP or threat intelligence platforms can help.
Preventing Future Exposure
While you can’t stop third-party services from being breached, you can:
- Implement enterprise password managers
- Use unique passwords across all accounts
- Deploy phishing-resistant MFA
- Conduct regular exposure assessments
CyberOne Can Help
From credential exposure assessments to red team exercises, we help organizations identify and mitigate weak points before attackers exploit them.
Let’s talk about how we can strengthen your external threat posture.
