As a web application penetration tester, I commonly come across applications using outdated software components, sometimes just a few versions behind, other times several years out of date. This issue almost always appears in client reports, since legacy plugins often contain multiple vulnerabilities.
In today’s digital landscape, web applications increasingly rely on JavaScript libraries to enhance functionality and user experience. Among these libraries, jQuery has long been a staple for developers due to its simplicity and robustness. However, as cybersecurity threats evolve, so do the vulnerabilities hidden in outdated components.
This led me to ask: Are these applications truly vulnerable, and can they be exploited on live production systems? To answer that, I built a Proof of Concept (PoC) to demonstrate whether the CVE-2022-31160 vulnerability in jQuery UI could be weaponized in real-world conditions.
My goal was to create a clear, lightweight PoC that would show clients why they need to patch, update, or replace insecure code instead of leaving web application security to chance.
Time constraints in assessments mean penetration testers can’t always bypass every Web Application Firewall (WAF) or customer security layer. But the risk is real: outdated libraries still surface in production today, leaving organizations open to attack.
This blog examines the critical CVE-2022-31160 vulnerability in jQuery UI, explains how it can be exploited, and shows why continuous vulnerability management is essential.
Understanding the CVE-2022-31160 Vulnerability
To understand the issue, I referenced the details at Snyk.io, then recreated the environment using Node.js, Express, and Docker.
The vulnerability exists in the jQuery UI checkboxradio widget, which is susceptible to Cross-Site Scripting (XSS). The problem comes from improper input handling: malicious scripts encoded in labels can be decoded when the widget is refreshed, enabling attackers to run arbitrary JavaScript.
The impact? Session hijacking, data theft, website defacement, or malicious redirection—all from a vulnerable widget.
Exploitation Walkthrough
For cybersecurity professionals, understanding how to identify and exploit these flaws is essential. We’ve published a full demonstration on GitHub so you can replicate it yourself:
CyberOne Offensive Security jQuery CVE-2022-31160 PoC
Prerequisites
- Linux distro
- Docker installed
- Web browser
1. Build and Run
Clone the GitHub project directory and build the Docker image locally. Once built, run the container to stand up the vulnerable environment.
2. Access the Demonstration
Navigate to:
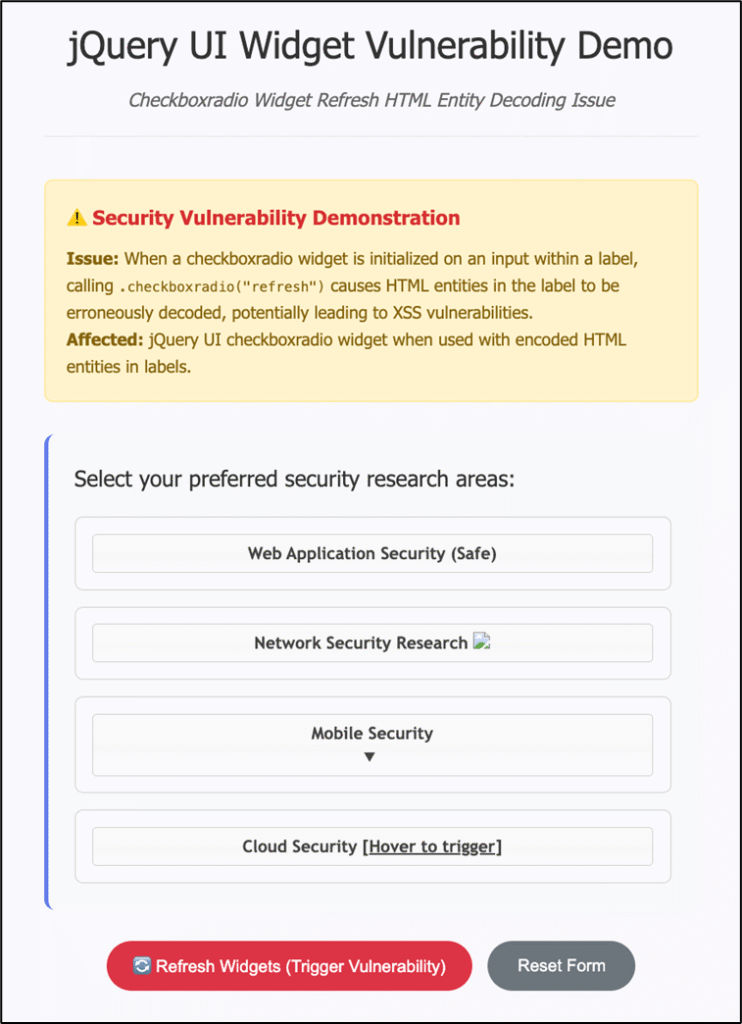
Vulnerability Overview
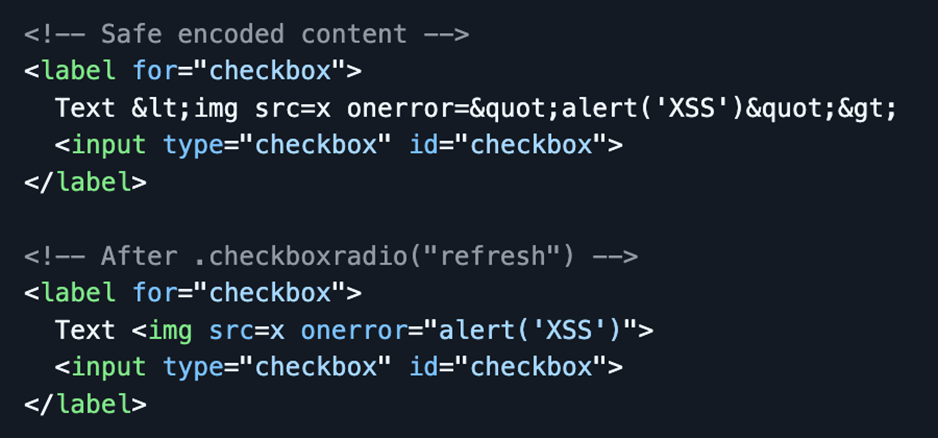
The jQuery UI checkboxradio widget is vulnerable to XSS via HTML entity decoding. When initialized on an input inside a label, calling .checkboxradio("refresh") decodes HTML entities in the label. Encoded malicious content is converted into executable JavaScript.
For the PoC, I built a simple survey form with four checkbox widgets:
- Safe Option – No encoded entities
- Network Security – XSS with
img srcpayload (immediate execution) - Mobile Security – XSS with
ontogglepayload (immediate execution) - Cloud Security – XSS with
onmouseoverpayload (interactive execution)
Upon loading the page jQuery UI initializes the checkbox widget. The Label content with encoded entities is processed. The .checkboxradio(‘refresh”) is called. jQuery Ui then decodes the HTML entities from the label, and the decoded malicious content becomes executable, and you see the reflected XSS execution.
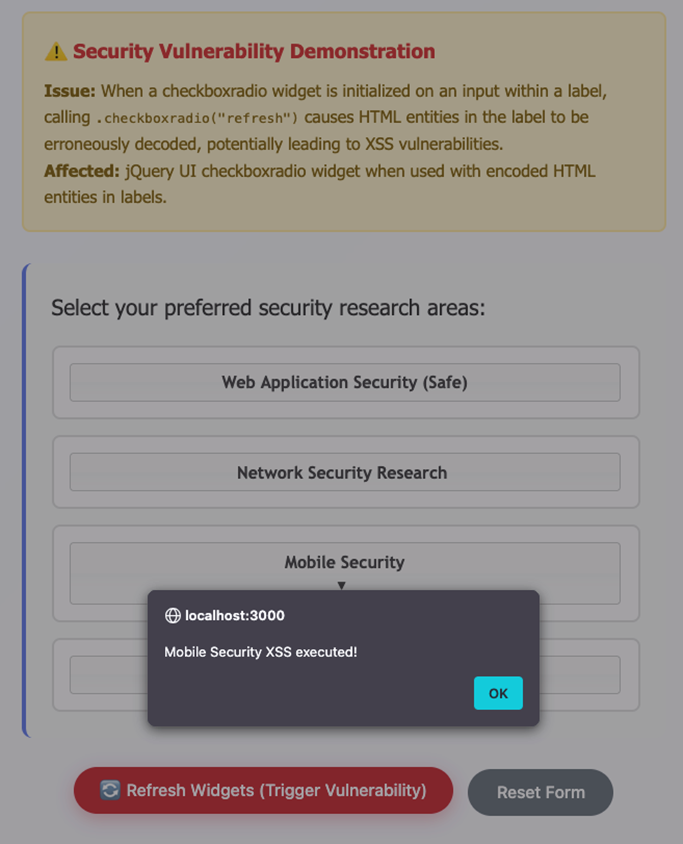
This vulnerability can be exploited in applications that use jQuery Ui checkboxradio widgets and allow user-generated content in labels. Applications that sanitize content using HTML entity encoding and programmatically refresh widgets.
Detection
To detect this vulnerability:
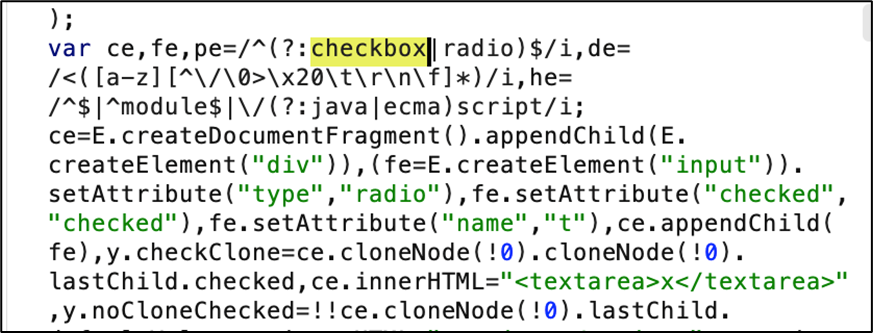
- Review JavaScript files for
.checkboxradio("refresh")calls. - Use browser developer tools to monitor label content changes. For dynamic analysis, monitor HTML content changes during widget operations.
- Capture traffic with Burp Suite and search for checkboxradio refresh functions in responses.
Mitigation
To fix the vulnerable component and reduce the risk associated with these vulnerabilities perform the following actions:
- Update jQuery UI to patched versions.
- Add server-side validation of user input.
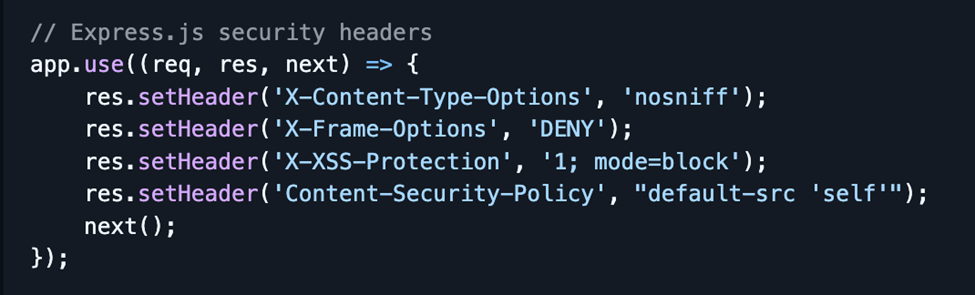
- Deploy restrictive CSP headers.
- Use context-appropriate output encoding.
Security Headers Example:
Final Thoughts
The CVE-2022-31160 vulnerability in jQuery UI highlights how outdated libraries silently undermine application security. While exploitation requires specific conditions, once met, the attack path is simple and damaging.
Key lessons:
- Dependency management = cybersecurity. Regular codebase reviews and patching are mandatory.
- Bake security testing into CI/CD pipelines to catch issues before deployment.
- Reinforce defense-in-depth with CSP, strong output encoding, and secure coding practices.
At CyberOne, our penetration testing services expose vulnerabilities like outdated jQuery before attackers exploit them. We help clients strengthen defenses with application security testing, exposure management, and proactive cloud security strategies that operationalize existing investments before adding new tools.
Plus, next time management or clients say that this type of vulnerability is irrelevant, an accepted risk, not that big of a deal, or too hard to mitigate, you’ll be able to demonstrate the actual impact and risk. Stay curious and happy hunting!
Don’t wait for attackers to test your apps first, let CyberOne show you the risks before they’re weaponized. Contact us today.
