Blog
Segmentation Often Starts Broad — But Rarely Goes Deep Enough One of the most common patterns we see in cloud security architecture is an early reliance on broad segmentation primitives,
As a web application penetration tester, I commonly come across applications using outdated software components, sometimes just a few versions behind, other times several years out of date. This issue
As your company grows, so does your reliance on cloud applications. Without proper oversight, cloud service usage can expose your organization to significant security vulnerabilities due to a lack of
Threat actors thrive on stolen credentials, and enterprise emails are often their top prize. While much attention is given to zero-days and vulnerabilities, leaked credentials from third-party data breaches are
Organizations are continuing to grapple with a cybersecurity talent shortage during a time of rapid growth of AI-driven threats. The rise in AI usage applies not only to security teams
In light of escalating global conflicts, increased nation-state activity, and widespread geopolitical instability, cybersecurity threats have intensified across many different sectors. All organizations should be proactively strengthening awareness and readiness
The days of securing digital identities with a simple password are over. Consider: 80 percent of all breaches use compromised identities, costing enterprises billions. And with SaaS applications and AI
On a recent internal penetration test, I was able to obtain Domain Admin privileges in a segmented network by calling on my ancient digital forensics skill set. I got my
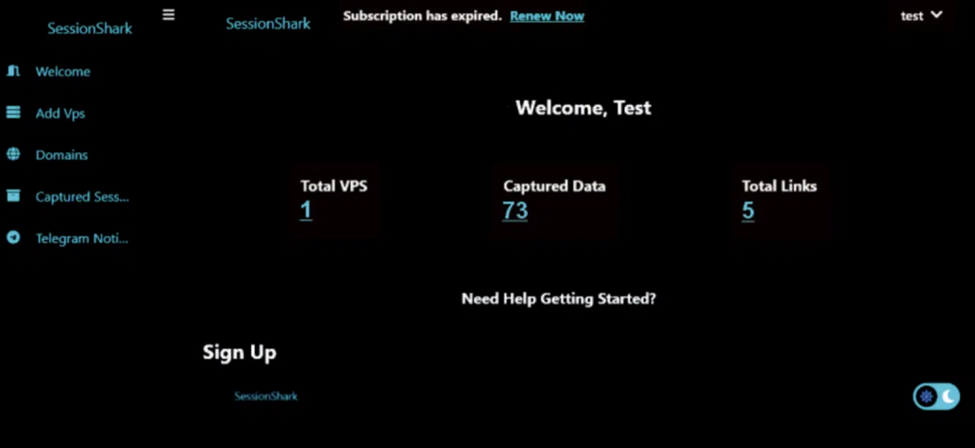
By Trevor Olson Recently, SlashNext (and many others) published an interesting article on ‘SessionShark,’ a phishing-as-a-service toolkit designed to steal session tokens and bypass Microsoft MFA. Their discussion around the